Safe Computing
How to stay Cyber-Safe
Note: This post is from October of 2022. While the information is still relevant, click here for the current CyberSecurity Month post
There are a lot of ways that hackers and other malicious actors can try to compromise your cybersecurity. With this constant danger, keeping yourself safe and secure online is extremely important. Below, you’ll find some helpful tips to be aware of whenever you’re browsing the web.
Be aware of where you are and what you click
When using the web, have a good idea of what it is that you want to accomplish. Before clicking through a website, spend some time familiarizing yourself with where the site’s buttons are, where ads are, and which buttons would likely take you to where you want to be. If you’ve spent some time making sure you know the layout of a webpage, you are much less likely to make errors in completing your tasks. Staying aware of how a site works also helps protect you from cybersecurity threats that prey on people not thinking about where they’re clicking.
Protect your identity
Many websites let you create accounts, where you build a digital identity with that site through a username. To protect your identity, make a username that doesn’t have personal information in it, such as your name, age, or location. If a website asks you to enter personal information, make sure you’re well informed about what the website is and how it will use the data that you provide it.
Check in with your antivirus software
If you use a windows PC, it has likely come equipped with Microsoft’s first-party antivirus program, which can be found in the Windows Security App. In order to make sure that you’re getting the most out of your antivirus, make sure to check its protection reports every now and then to see if you need to take any actions to protect your PC. It’s also a good idea to check your device for any updates, which can provide important security features to help protect your system from current threats. For more information on antivirus software, check out our article on the topic.
Make strong passwords
Your passwords should be regularly updated, and difficult for others to remember. It’s good practice to use a different password for each program that you use, as a compromised password can easily lead to data theft. If you need help making a strong password, try using Missouri S&T’s password requirements. Following these will help ensure that your passwords are as strong as possible, which adds another level of protection to your data.
Have a backup of your data
In order to prevent cyberattacks or computer malfunctions from compromising your data, have a backup of important files stored on a separate storage device. This helps keep your data physically safe from anything that might try attacking your primary drive. For extra security, keep your backup drive unplugged from your computer entirely. This will further protect it from any hazards that might occur on your computer, ensuring that you always have access to the files you need if and when you need them.
Know how hackers operate
Many large data thefts don’t involve anything close to what we might picture when we imagine hacking. Many hacks rely much more on tricking employees into providing data (or at least access to data) through social engineering. Phishing is one of the more popular ways that a malicious actor can use to try to steal data or other sensitive information. These attacks involve the attacker acting like a trustworthy source to trick someone into giving away information or data. Read this article about how one phishing attempt targeting researchers used fake senders as well as fake responders to make the scam appear more trustworthy. Another article finds that most successful phishing attacks are ones that impersonate HR, IT departments, or even other employees in order to build a false sense of trust in the victim. Missouri S&T is no stranger to phishing attacks, so keeping our campus aware of how these scams operate is of the utmost importance. Knowing how to detect a phishing scam helps keep all of us safe from harmful cyberattacks and data breaches. See our article about phishing for more information.
But I’ll only be gone for a second: lock your computer
I am just going to be a short distance away, and I can see my computer from here you may think. What if a quick jaunt away from your desk turns into a thirty-minute conversation after an unexpected run-in with an old friend? Or what if you’re at work heading to the printer to quickly grab the printout and you get stopped by your manager requesting an update on your projects? It’s unexpected moments like these when leaving our computer screen unlocked may result in an invasion of your privacy or a breach of security.
But I use a screensaver
There is a window of time during which your screen may dim before the screen saver appears. During this dim period, your computer may look locked, but it is not. Someone can walk up and press any key or button on your computer to “wake” up the screen. Now they have full access to the information stored there. This could leave you to face the consequences of leaked confidential or personal information.
Protect your confidential and personal information
If you leave your computer screen unlocked while you have work documents or personal accounts open on your computer when you walk away, anyone can come by and steal information or make changes to your account without your knowledge. You never know when you may have guests walk through the halls of your living space or office, or when a stranger at a coffee shop may stroll by. By leaving your computer screen unlocked you have given all of them full access to the information you have stored on your computer. Simply locking your computer screen can help keep confidential information private and keep you out of trouble.
Therefore, leaving your computer unattended is like surrendering access to your whole computer – all the files, the open software, and the logged-in account – to someone unauthorized to see them. Every unexpected second you spend away from your computer is a second someone else has with your data. Locking your computer screen when you step away, even for a moment, keeps your data safe and secure and is something you can implement in your daily routine.
How Do I Lock My Computer?
Make a habit of locking your computer every time you step away, even for a moment, with this simple keypress:
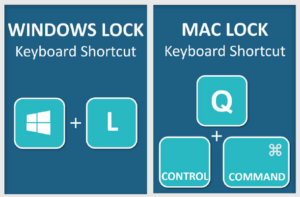
UM System lists minimum security requirements when using campus computers in order by Data Classification Levels (DCL). All 4 levels require you to lock your computer screen when unattended.
I think my machine is compromised! What should I do?
Imagine waking up in the morning to find an intruder living in your house, wearing your pajamas, eating out of your refrigerator, using your bank account, and answering the phone pretending to be you every time it rings. Maybe your initial reaction is to keep the situation to yourself because you don’t want to have to explain to anybody where the intruder got the panda onesie from, but you can’t ignore the fact that an intruder is living in your house. You would probably lock yourself in a room and call for help.
This scenario may seem a little extreme but it is identical to the situation you might find yourself in when your computer gets compromised. However, the longer you wait to fix the issue, the more the compromise may spread beyond your computer and your accounts.
What should you do?
The problem won’t go away until you report and clean up the compromise.
Personal Computer
If this happens on your personal computer:
- Shut down your computer.
- Contact a local computer support professional.
- From another computer or device, change your passwords on all the accounts you’ve logged into from that computer. If you have used campus resources on that computer, you will need to change your campus password and report the incident to S&T IT Security.
Campus Computer
If your campus computer is compromised, follow the steps below:
- Shut down your computer.
- From another computer or device, change your campus password.
- Report the incident to S&T IT Security.
It is essential that all university faculty, staff, and students should immediately report a security incident to improve the overall security environment.
See UM’s Information Security Mandatory Reporting Requirement Policy>>
Three Steps to Make Yourself Cyber Safe
The Federal Trade Commission’s (FTC) data shows that 2020 had 1.4 million reported identity thefts, and they expect it to increase in 2021. These thefts mainly occur due to outdated software and weak passwords. There are three steps below that you can follow to improve your cyber security.
1. Keep your antivirus software up to date
Personal computers are used for many things such as emailing, messaging, moving funds between bank accounts, going on social media, doing your taxes every year, browsing the web, and more. Therefore, keeping your personal information secure and safe from malware is important. One way to keep malware at bay is to use antivirus software that will detect and remove malware from your computer.
Keep in mind that you need to keep all software up to date so that the computer runs well and helps to keep your information safe. Some antivirus software makes that easy by allowing you to choose automatic updates but you have to search for it in the settings.
It only takes a few minutes to locate and turn on the automatic updates of your existing antivirus software or to install the antivirus software of your choosing to keep you cyber safe.
Recommended Antivirus Software:
Windows
- Microsoft Windows Defender (comes with all Windows 10 computers)
- MalwareBytes
- Norton Antivirus
Mac
2. Use a password manager
Passwords are one of the biggest vulnerabilities when it comes to keeping your personal information safe and secure. One way to create and update a strong password is by using a password manager. A password manager is a software application designed to safely store and manage your passwords with encryption. The benefit of using a password manager is that all you need is a single, master password for the manager and you are able to access all the passwords you have saved. Password managers can remind you when it’s time to update your password and notify you if your password may have been compromised. If you aren’t sure that your password is strong enough, a password manager can also help create a password that isn’t associated with your personal information so it is harder to hack.
To use the tool, all you would need to do is pick the password manager that works best with your computer’s operating system – Windows or Mac – and install it. Then you create a master password and start storing your passwords for other software and applications. We do recommend allowing the password manager to create or suggest passwords for you.
Recommended Password Managers:
Windows
Mac
3. Update your Browser
Keeping your web browser up to date by making sure you have all the newest security patches installed is also important when it comes to practicing safe browsing. Computer Hope has step-by-step instructions on how to check for updates for the 6 most common web browsers.
By following all three steps of updating your antivirus, using a password manager, and keeping your browser up to date, you can improve your cyber safety and avoid being one of the reported identity thefts.